EKS Best Practices
Complying with a Kubernetes cluster best practice on AWS can be challenging for an organization as it requires a strong understanding of Kubernetes and AWS. This can include the ability to properly configure and manage the cluster, ensure its scalability and availability, and secure it from potential malicious attacks. It also involves the integration with other AWS services and the ability to monitor and troubleshoot the cluster effectively.
Retrieve WhitepaperReputable EKS Partner
Amazon Web Service has announced us as one of the initial EKS delivery partner.Official Announcement

Best Practice

Network Policies for Security

Monitor with Promestheus/Grafana

Authentication and Authorization with IAM

Secrets Management for Sensitive Data

Cost Optimization

Namespaces for Isolation

Configure Resource Quota

Backup and versioning

Patch Worker Nodes

Infastructure as Code (IaC)
What are the benefits

Enhanced Security
By implementing practices such as IAM roles for access control and network policies for pod communication, your organization can better protect its data and resources.
Improved Efficiency
Utilizing Kubernetes Namespaces for resource isolation, implementing resource requests and limits, and using autoscaling can optimize your organization's resource usage and improve overall performance.
High Availability
Regularly backing up and versioning your cluster state and updating worker nodes can help ensure quick recovery from any issues that may arise.
Advanced Monitoring
Using tools such as Prometheus and Grafana can provide better visibility and effective troubleshooting of any issues that may arise.
Reduced Costs
Implementing autoscaling for resources, separating workload with various instances type or spot instances, and using the latest version of Kubernetes can help reduce costs associated with over-provisioning or underutilization of resources.

Stay up-to-date
Staying on the latest version of Kubernetes and regularly updating worker nodes can ensure that your organization benefits from the latest features and security updates.
Check out our latest EKS Blogs
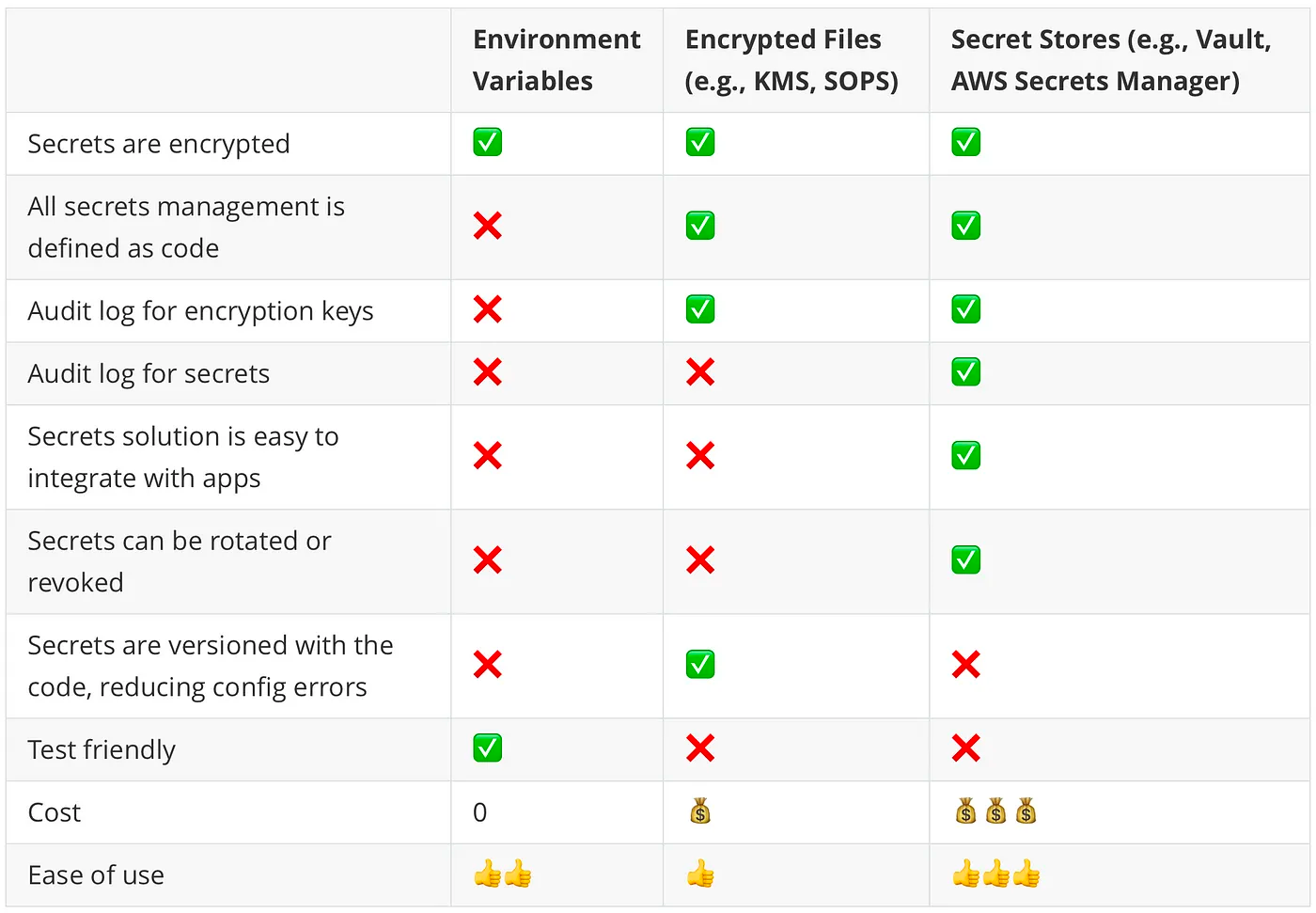
EKS Best Practice - Store Secrets for Sensitive Data
A Kubernetes Secret is an object that contains a small amount of sensitive data such as a password, a token, or a key. Such information might otherwise be put in a Pod specification or in a container image...
Read More
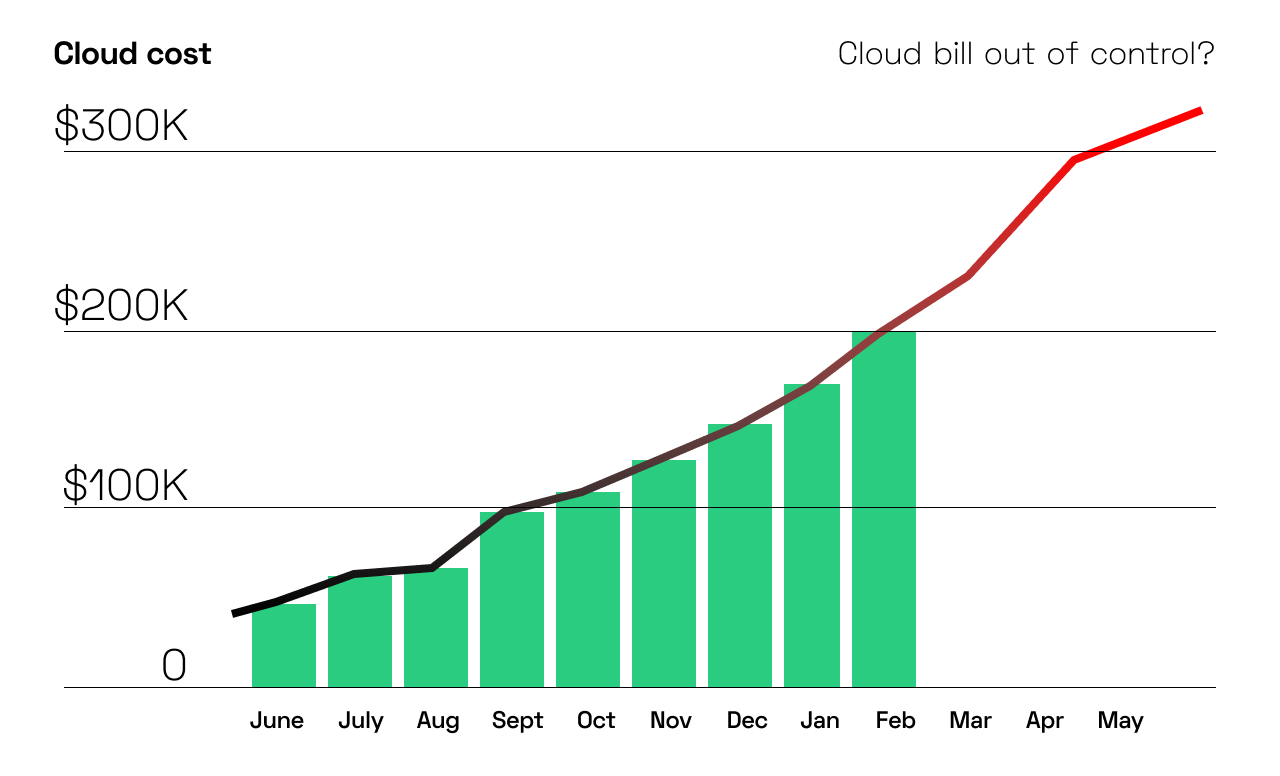
EKS Best Practice - Cost Monitoring on Specific Workload
Learn how Kubernetes Cost Monitoring can help organizations track and analyze expenses associated with running applications and services on Kubernetes clusters…
Read More
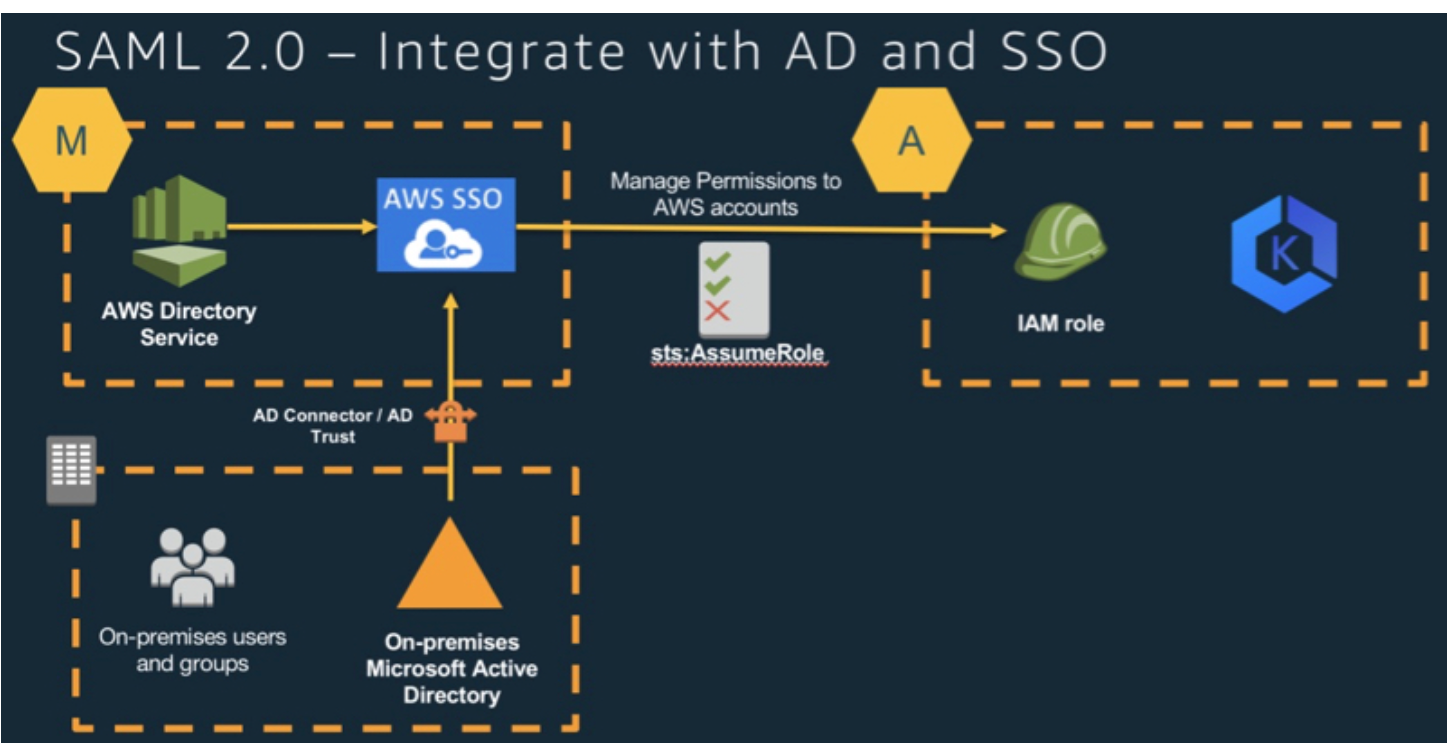
EKS Best Practice - SSO Integration
Single Sign-On (SSO) is widely used in organizations and companies. In this article, we are going to talk about the best way to integrate SSO with EKS clusters, with the best EKS cluster authorization...
Read More